User Activity Monitoring
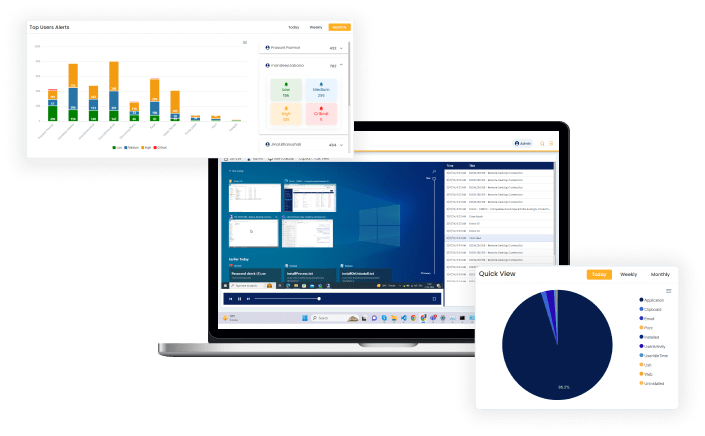
Monitoring Features
Video Recording
This feature enables the system to record video from the monitored devices. It allows administrators to review recorded content for security, compliance, or training purposes.
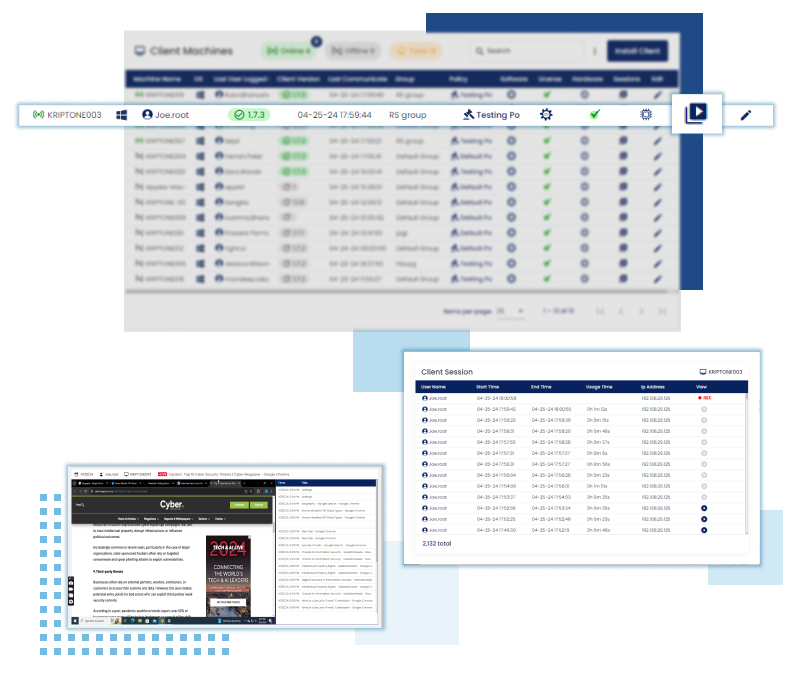
End-User Activity Report
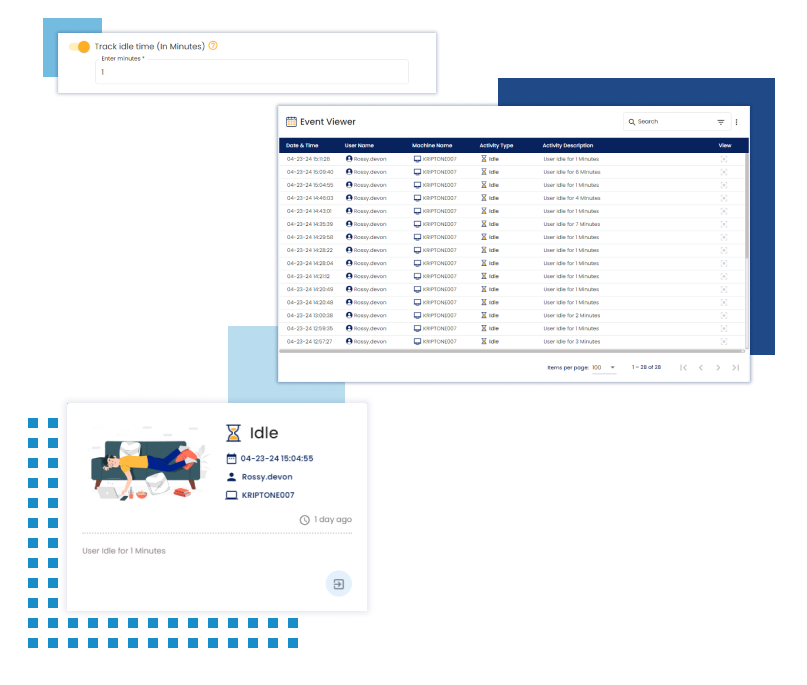
Idle Time Monitoring
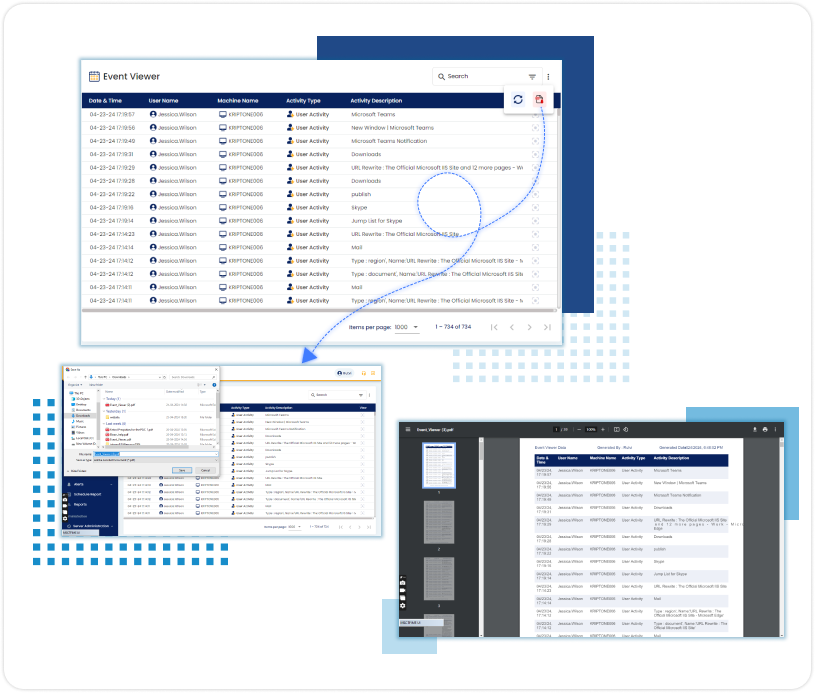
Session Activities (Log In/Log Out)
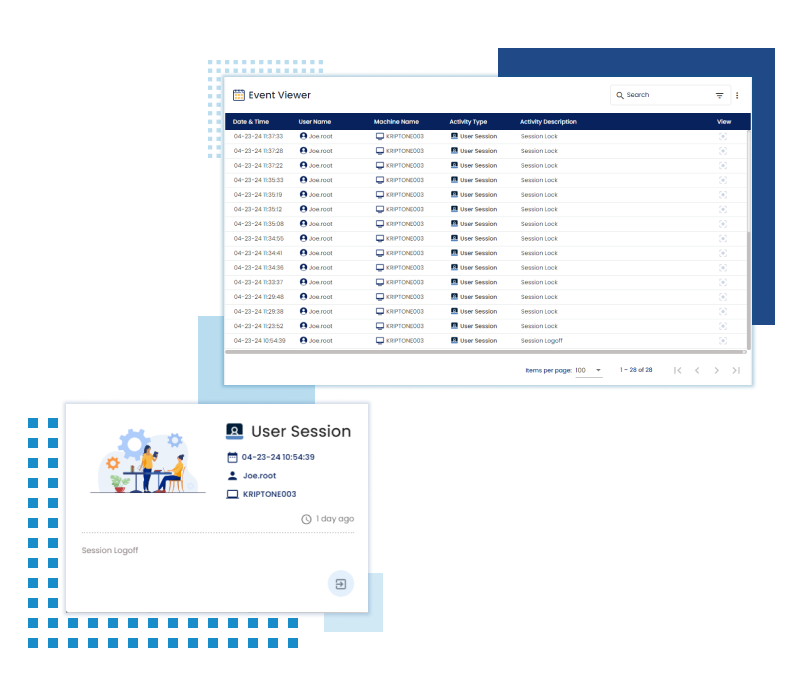
Capture Screenshots Taken
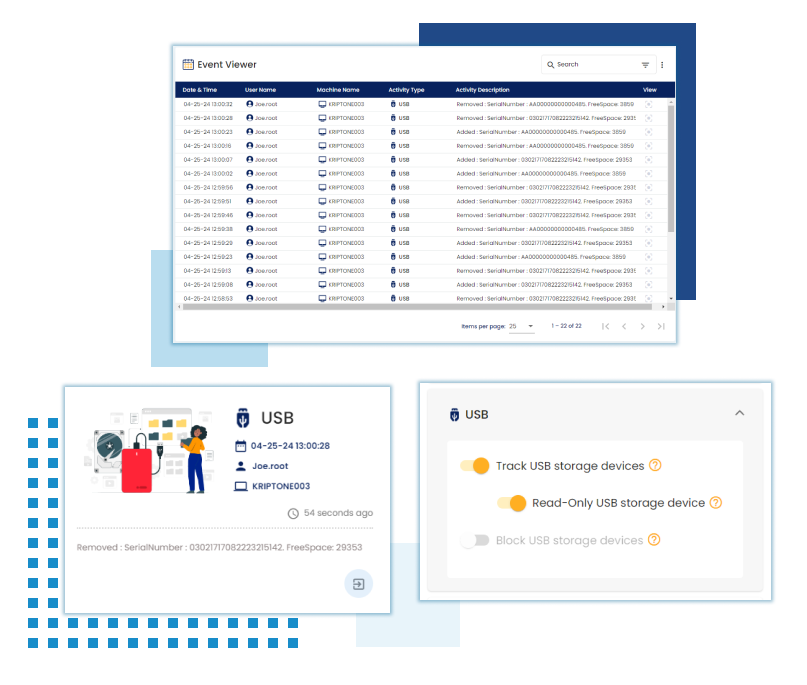
USB Monitoring
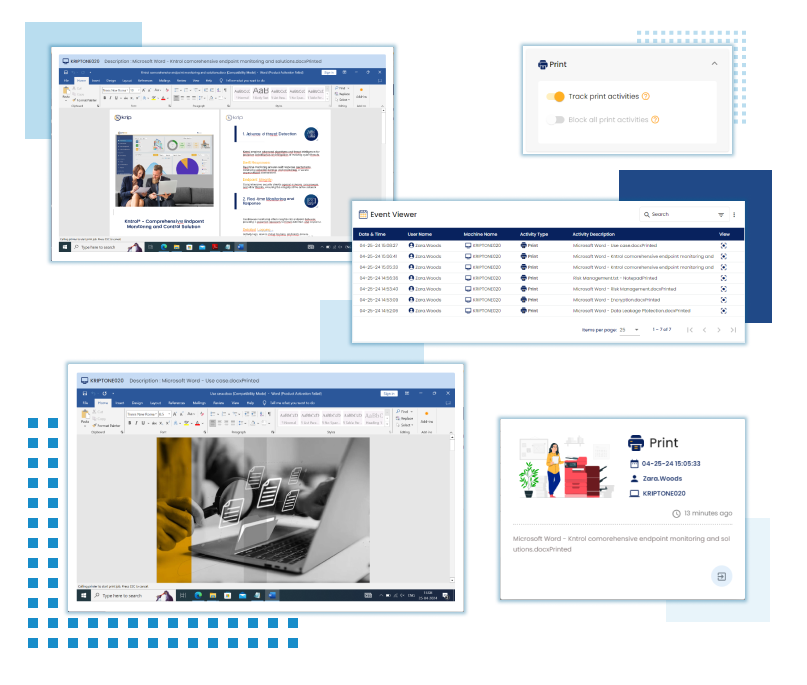
Print Tracking
Tracking Clipboard Data Transfer

Email Activities
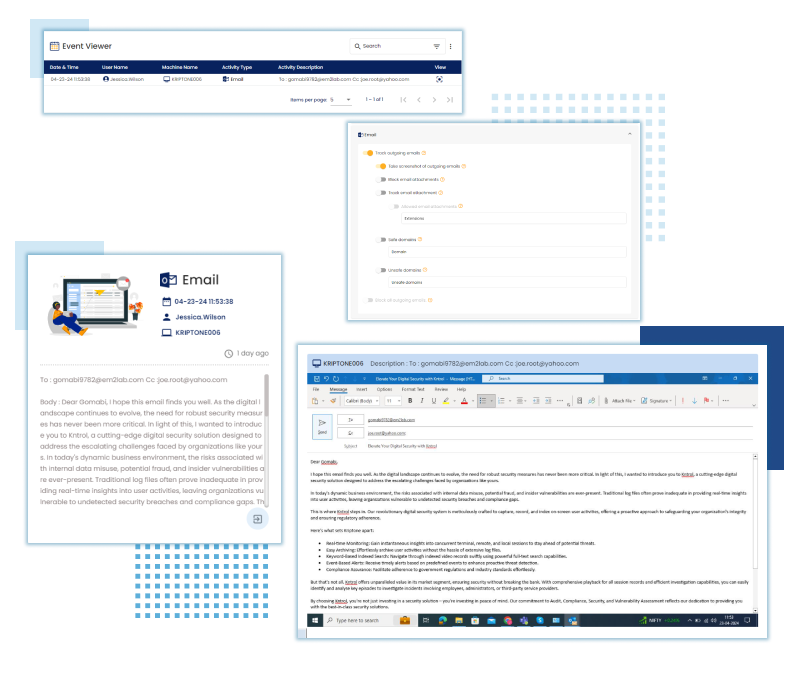
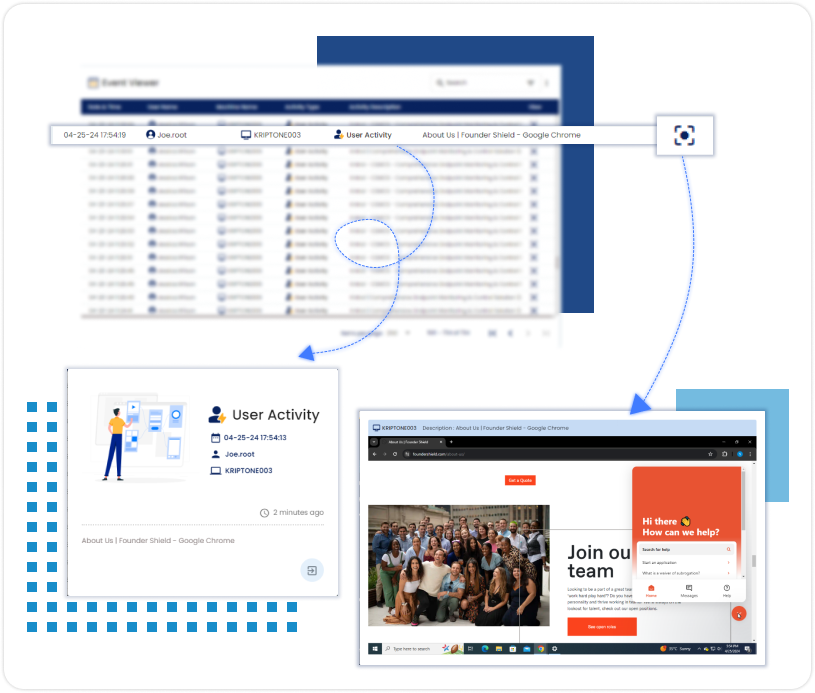
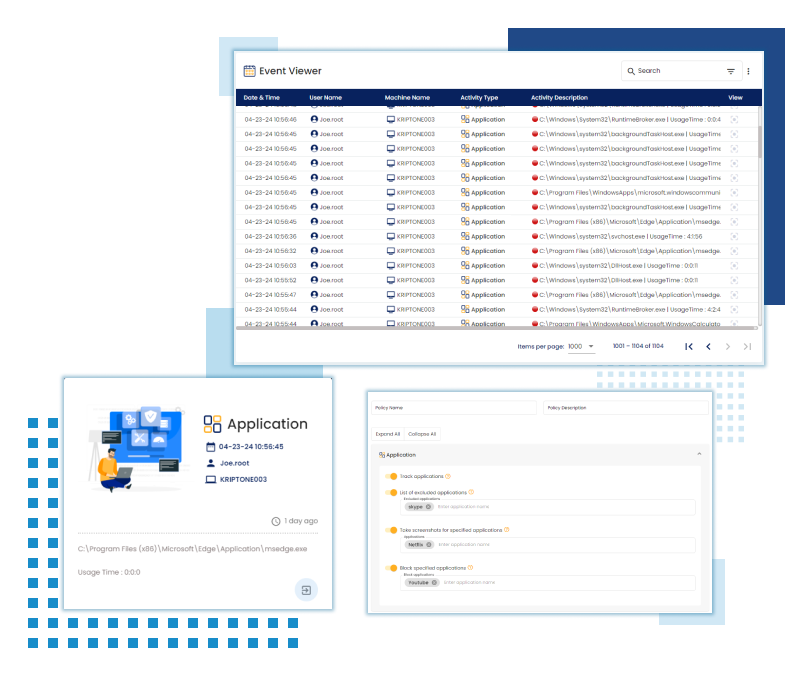
Application Monitoring
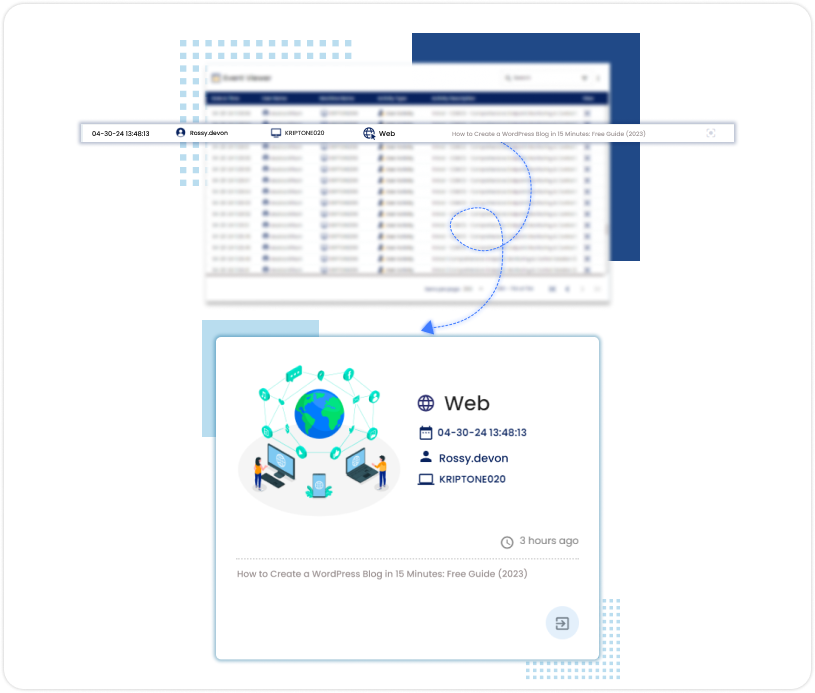
Web Tracking
Controlling And Blocking Features
Application Control
Enables administrators to control which applications users can access and use on their devices. It helps enforce security policies and prevent unauthorized software installations.
USB Control
Allows administrators to control and restrict the use of USB devices on monitored endpoints. This helps prevent data leakage and mitigate the risk of malware infections via USB drives.
Two-Factor Authentication
Enhances security by requiring users to provide two forms of authentication before accessing sensitive systems or data. It adds an extra layer of protection against unauthorized access.
File Tracking
Tracks file access and modifications, including details such as file names, locations, and users who accessed or modified the files. Useful for auditing and compliance purposes.
Automatic Watermarking on Screen Capture
Automatically adds watermarks to screenshots taken on monitored devices. This helps prevent the unauthorized distribution of sensitive information captured in screenshots.
Screenshots Restriction
Restricts or controls the ability to capture screenshots on monitored devices. Useful for protecting sensitive information and preventing data leaks.
Print Blocking
Allows administrators to block or restrict printing activities on the monitored devices. Useful for controlling printing costs, preventing unauthorized document printing, and enforcing printing policies.
Reporting Features
Alerts
Generates real-time alerts based on predefined criteria or security events. Alerts can notify administrators of potential security breaches, policy violations, or system anomalies.
Risk Ranking
Ranks security risks or incidents based on severity levels or impact factors. This helps prioritize responses and allocate resources effectively to mitigate the most critical risks first.
Policy Scheduler
Allows administrators to schedule and automate policy enforcement actions. This ensures that security policies are consistently applied and maintained across all monitored devices.
Reports
Generates customizable reports summarizing monitoring, controlling, and blocking activities. Reports provide insights into user behavior, compliance status, security incidents, and overall system performance.
Advance Features
FILE MONITORING
The file monitoring feature tracks and manages file activities like creation, modification, renaming, and deletion to maintain security and data integrity. Users can configure it to focus on specific folders and file types while excluding others, optimizing monitoring efficiency.
CONTENT SCANNING
The “Content Scanning” feature in security and data management tools allows users to monitor and analyze files within a system or network. It offers configurable options to target specific folders and file types, while also excluding certain directories and file extensions, optimizing resource use and focus on critical data.



