Comprehensive Endpoint Security Solution
Kntrol: Endpoint security solution guards against insider threats, ensures compliance, and enables proactive breach prevention with advanced features.

Monitoring Features
Audio/Video Recording
Detect and prevent unauthorized audio/video recording within the endpoint environment, safeguarding sensitive information and ensuring privacy compliance.
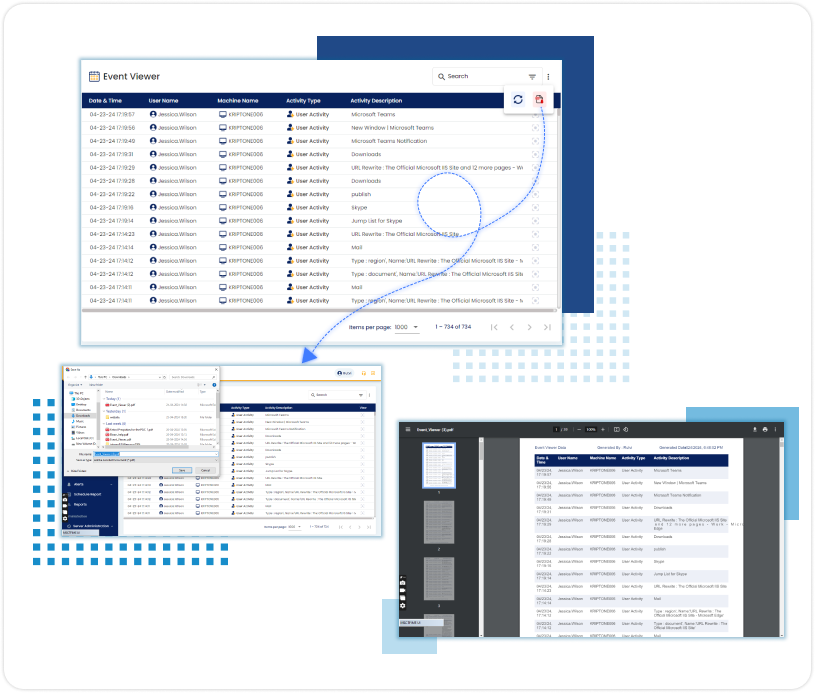
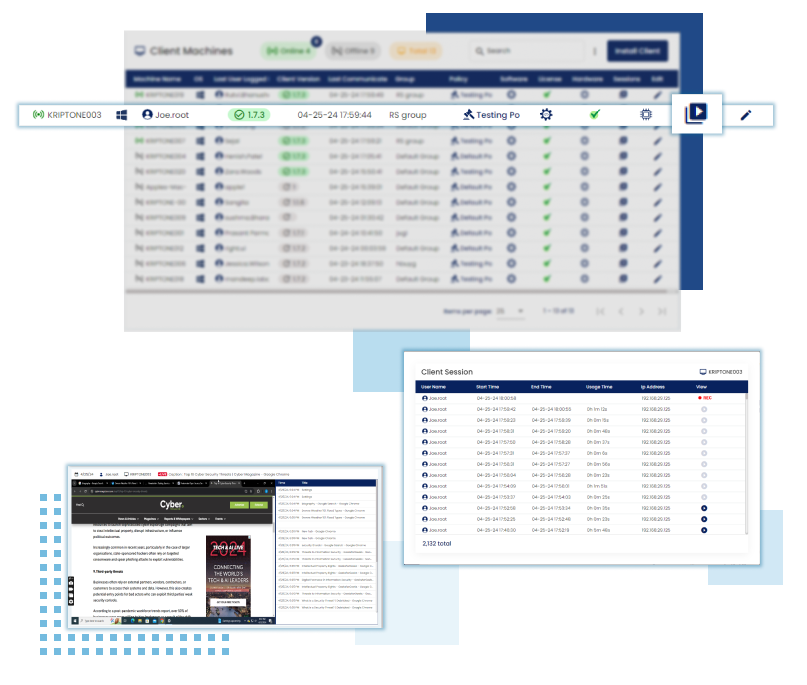
End User Activity Report
Generate detailed reports on end-user activities, enabling administrators to track user behaviour, identify anomalies, and enforce security policies effectively.
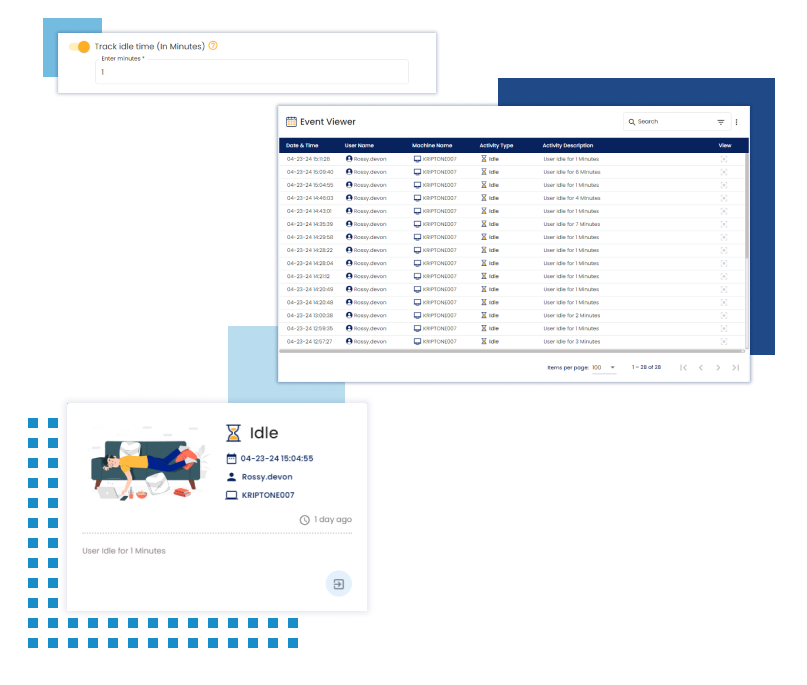
Idle Time Monitoring
Monitor idle time to detect potential security breaches or unauthorized access during periods of inactivity, enhancing endpoint security posture.
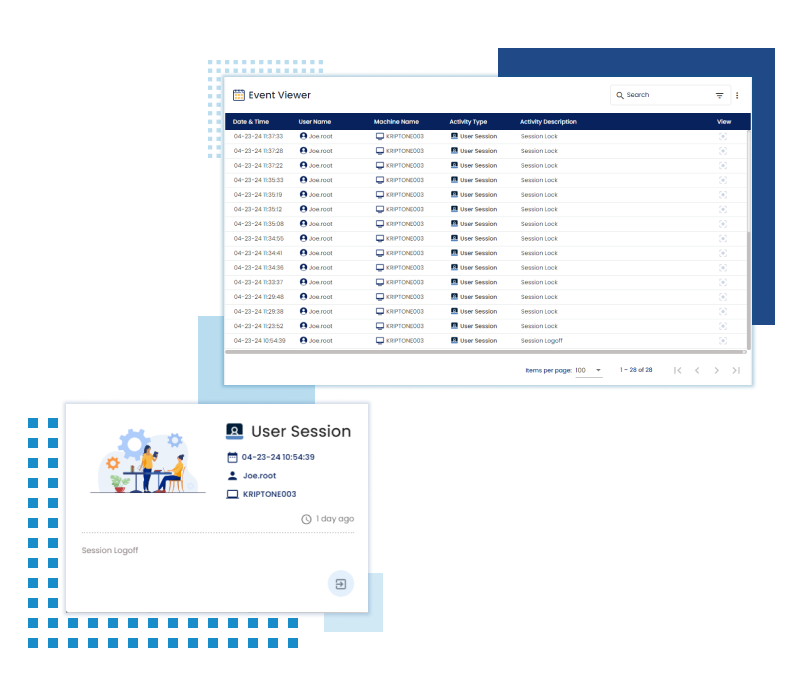
Session Activities
Log all user login and logout activities to track user sessions, identify suspicious behavior, and facilitate forensic analysis in the event of security incidents.
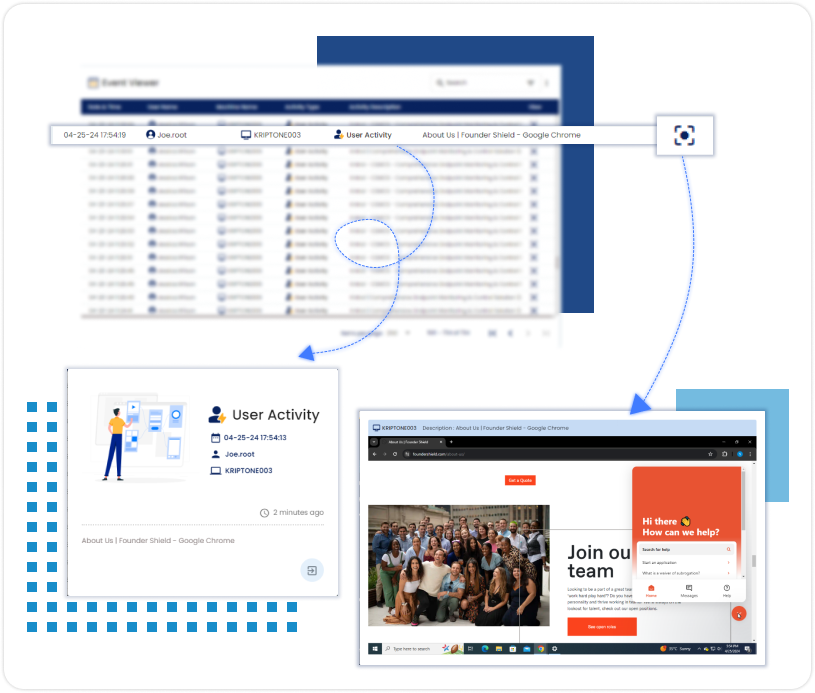
Capture Screenshots Taken
Capture screenshots taken by users to provide visual evidence of endpoint activities, aiding in investigations and ensuring compliance with security policies.
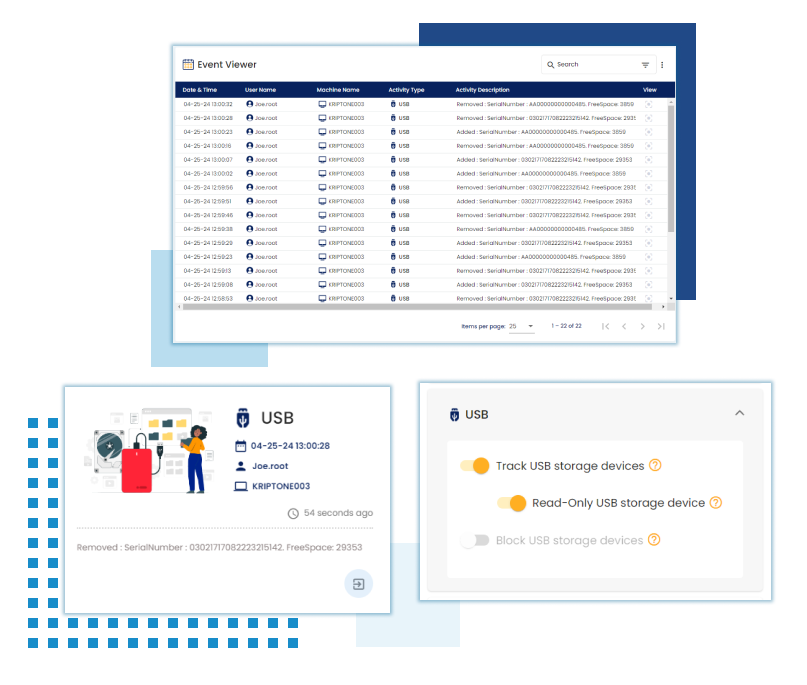
USB Monitoring
Monitor USB device usage to prevent data exfiltration through unauthorized external devices, enhancing data loss prevention measures.
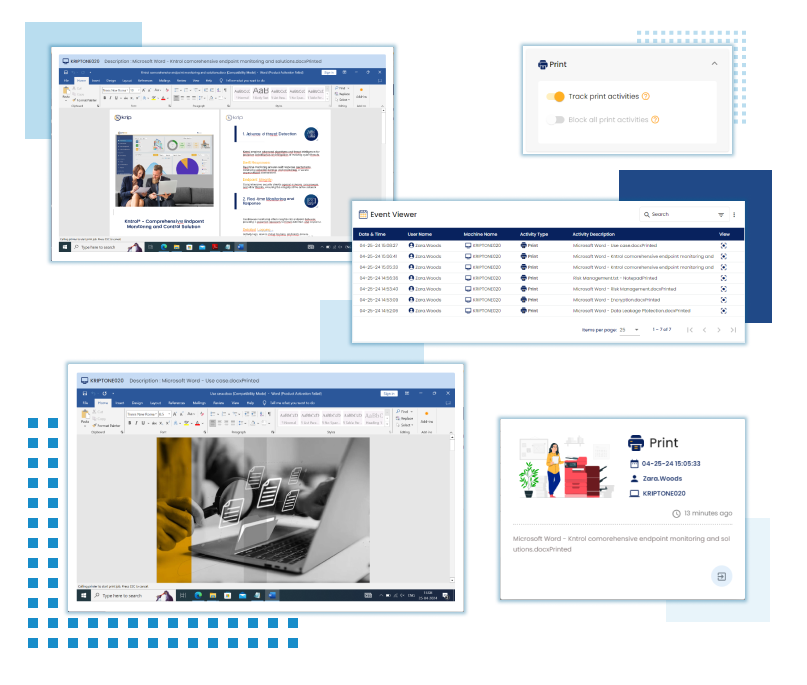
Print Tracking
Track printing activities to monitor document flow, prevent unauthorized printing of sensitive information, and enforce print security policies effectively.

Tracking Clipboard Data Transfer
Monitor clipboard activities to prevent unauthorized data transfers or leakage of sensitive information through copy-paste operations, ensuring data protection.
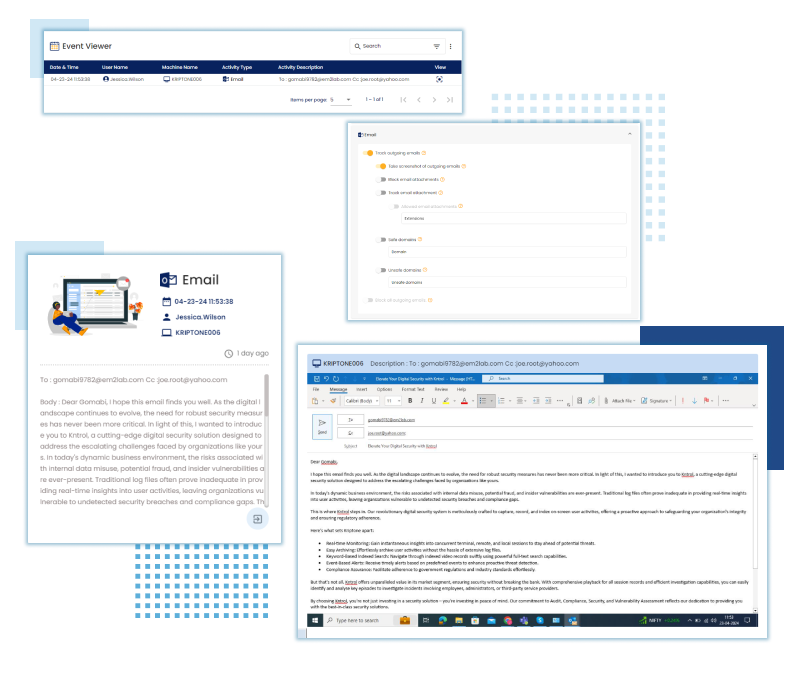
Email Activities
Monitor email communications to detect and prevent phishing attacks, data leakage, or unauthorized transmission of confidential information, enhancing email security.
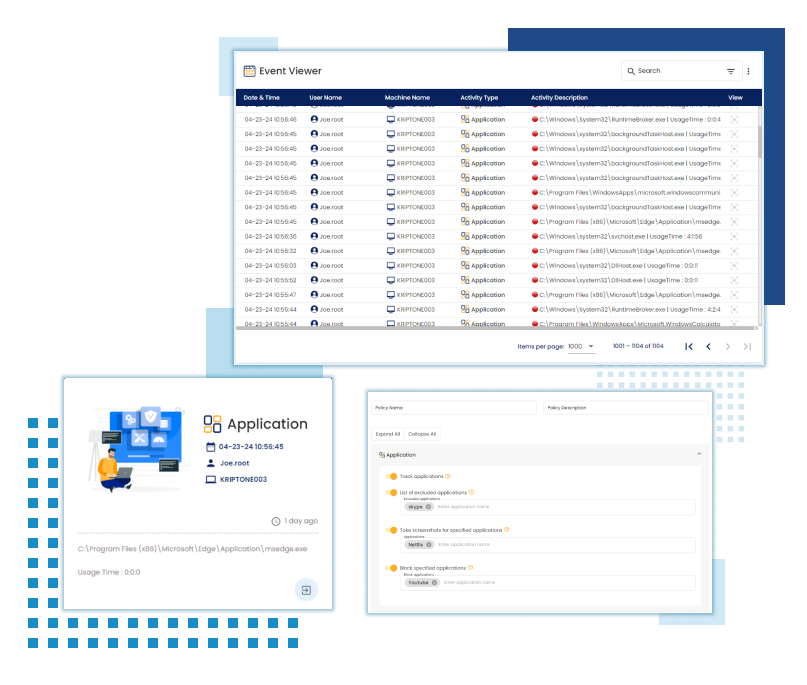
Application Monitoring
Monitor application usage to detect suspicious or unauthorized software installations, enforce application control policies, and mitigate risks associated with unapproved applications.
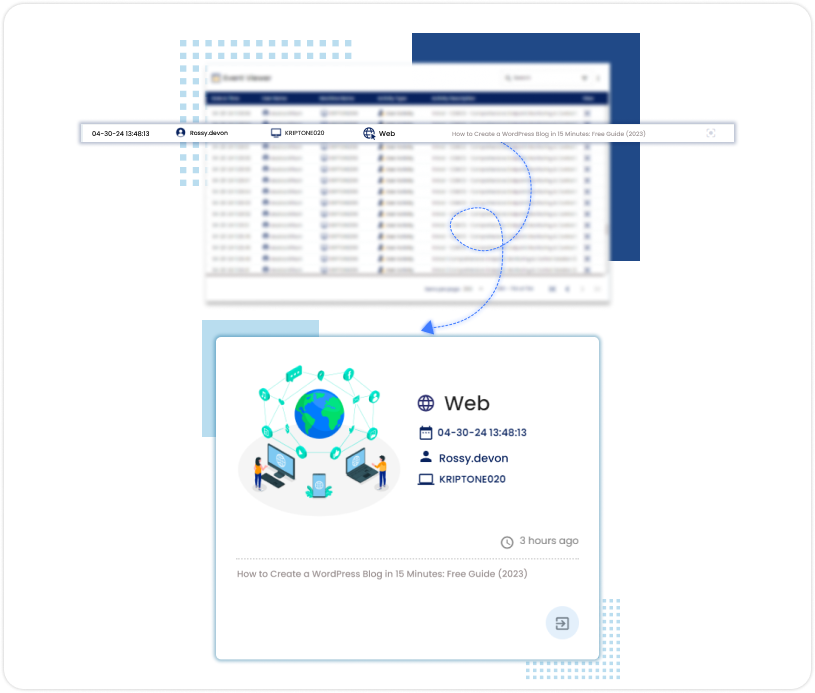
Web Tracking
Track web browsing activities to enforce acceptable use policies, block access to malicious websites, and prevent downloads, enhancing the web security posture.
Reporting Features

01 Alerts
Generate real-time alerts for security incidents, policy violations, or suspicious activities to enable immediate response and remediation actions, enhancing threat detection and incident response capabilities.
02 Risk Ranking
Rank security risks based on severity and impact to prioritize remediation efforts, allocate resources effectively, and mitigate the most critical vulnerabilities or threats first.
03 Policy Scheduler
Schedule automated policy updates, scans, or maintenance tasks to ensure continuous protection, compliance with security policies, and optimal performance of endpoint security controls.
04 Reports
Generate comprehensive reports on security events, compliance status, and endpoint activities to facilitate auditing, regulatory compliance, and management decision-making processes.
Controlling And Blocking Features
Application Control
Control access to applications based on predefined policies, restrict execution of unauthorized applications and prevent malware proliferation through application whitelisting/blacklisting.
USB Control
Implement granular controls over USB device usage, including blocking specific devices or restricting data transfer, to prevent data breaches and malware infections via USB ports.
Print Blocking
Block printing of sensitive documents or specific file types to prevent unauthorized disclosure of confidential information and enforce print security policies effectively.
File Tracking
Track file access and modifications to detect unauthorized activities, prevent data exfiltration, and ensure data integrity and confidentiality.
Automatic Watermarking on Screen Capture
Automatically embed watermarks on captured screenshots to deter unauthorized distribution or manipulation of sensitive information, enhancing intellectual property protection.
Screenshots Restriction
Restrict the ability to take screenshots of sensitive or confidential data to prevent information leakage and maintain privacy compliance.
Two-Factor Authentication
Implement two-factor authentication to strengthen endpoint security by requiring an additional layer of verification, mitigating the risk of unauthorized access or credential theft.



