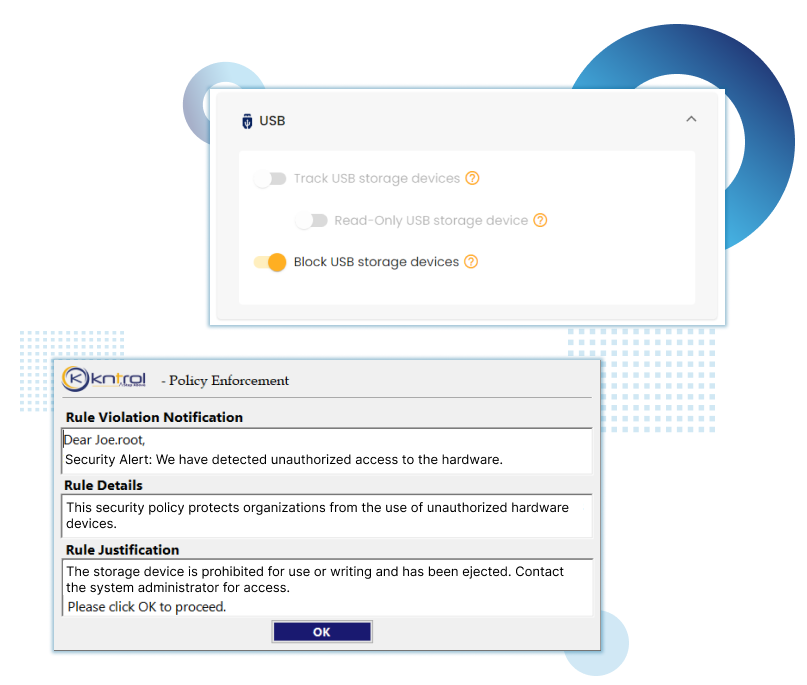
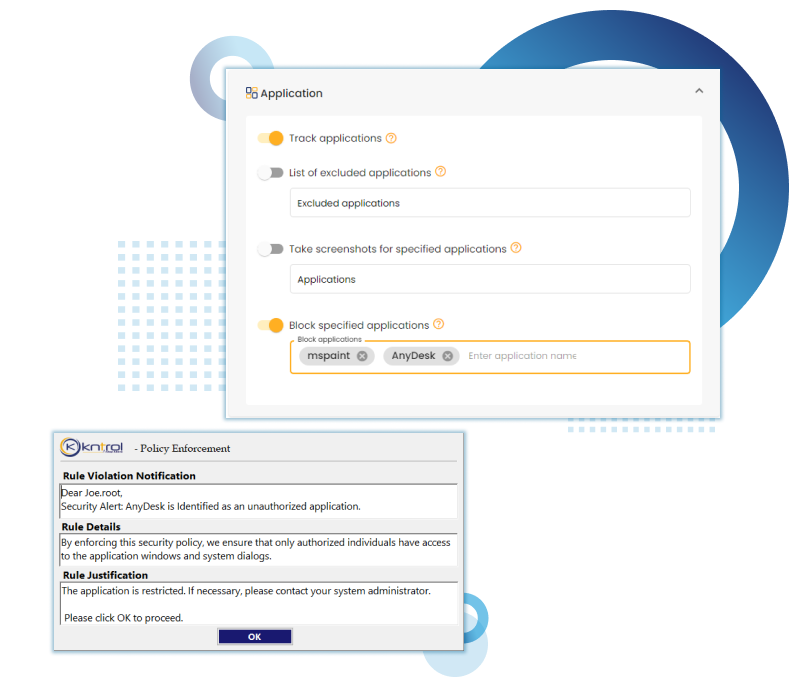
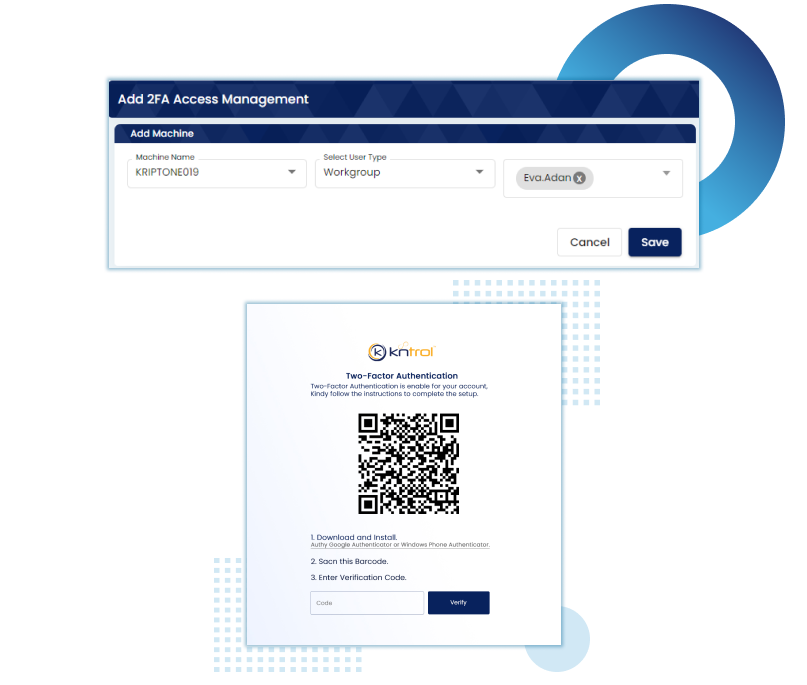
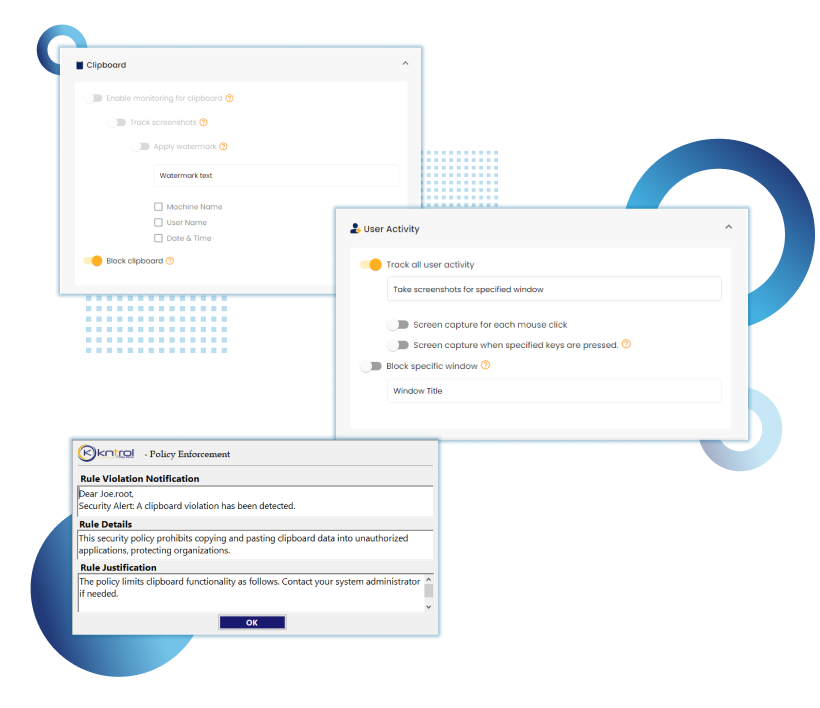
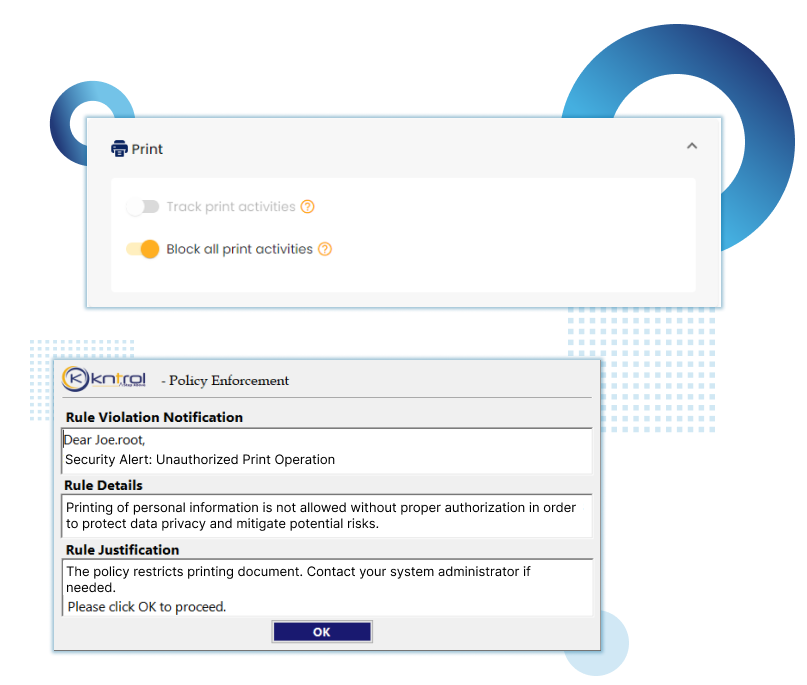
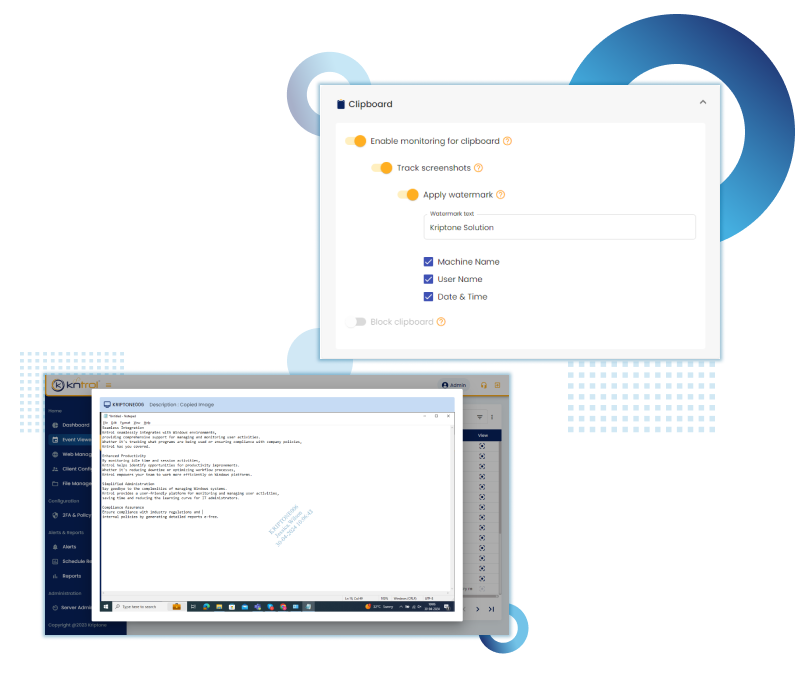
Kriptone leads the Insider security industry with advanced endpoint monitoring, ensuring top-notch organizational safety. Trusted for excellence, it’s the preferred choice for cutting-edge security solutions.

ABOUT
PRODUCTS
USE CASES
© 2026 Designed and Developed By Kriptone

Kriptone leads the Insider security industry with advanced endpoint monitoring, ensuring top-notch organizational safety.

ABOUT
PRODUCTS
USE CASES
© 2026 Designed and Developed By Kriptone

Kriptone leads the Insider security industry with advanced endpoint monitoring, ensuring top-notch organizational safety. Trusted for excellence, it’s the preferred choice for cutting-edge security solutions.

USE CASES
© 2026 Designed and Developed By Kriptone