Data Loss Prevention (DLP)

Monitoring Features
Audio/Video Recording
Implement audio and video recording capabilities to monitor and detect sensitive data being shared through multimedia formats.
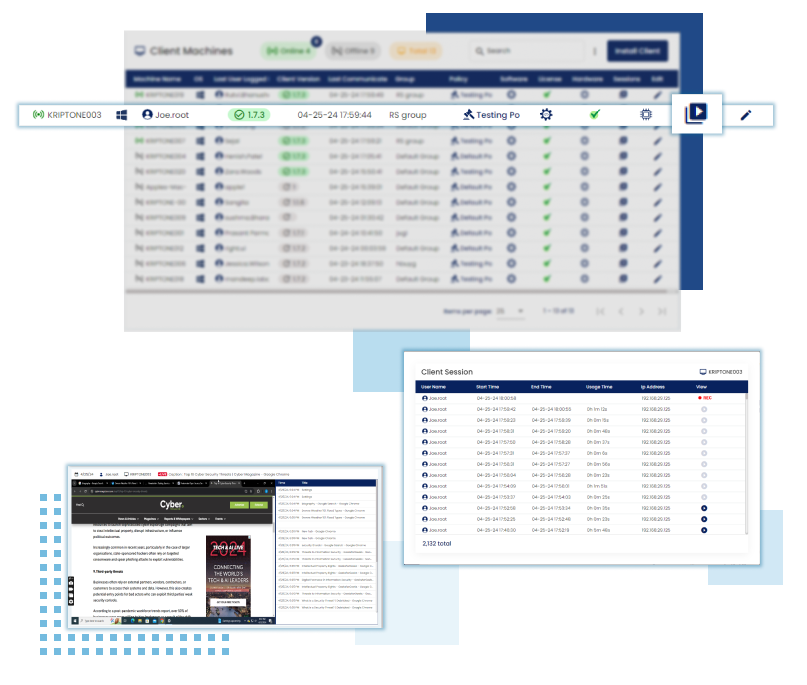
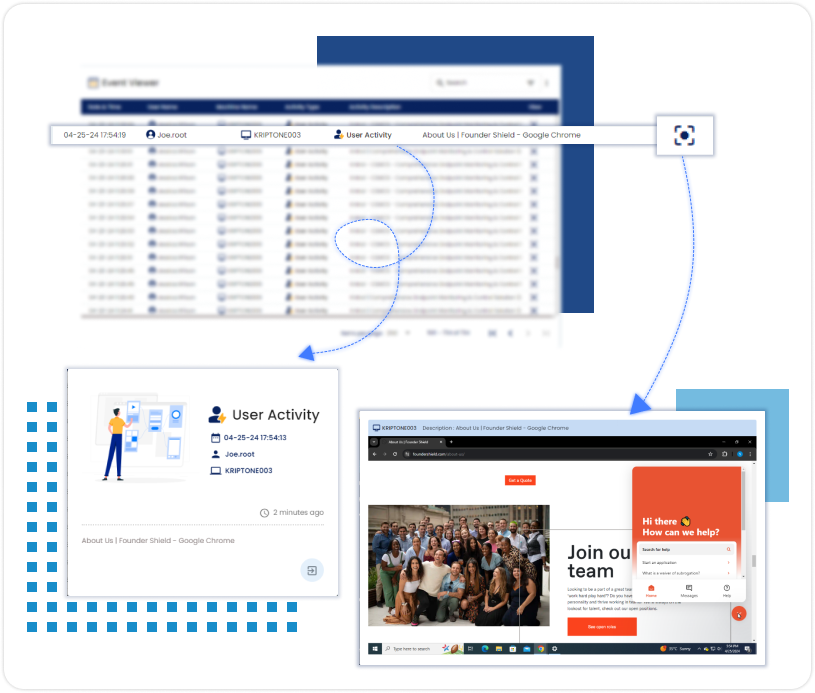
End-User Activity Report
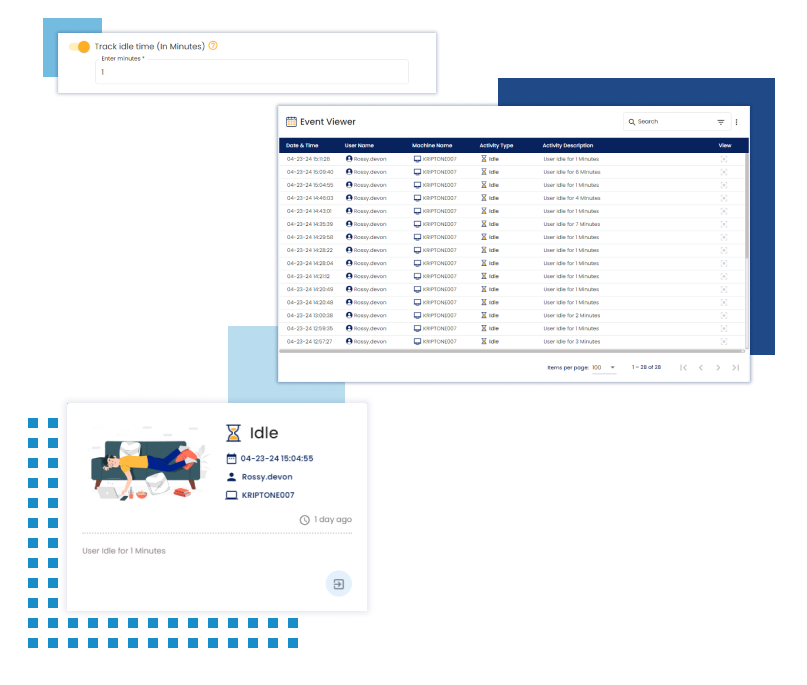
Idle Time Monitoring
Detects prolonged idle time periods and triggers alerts to prevent unauthorized access to sensitive information.
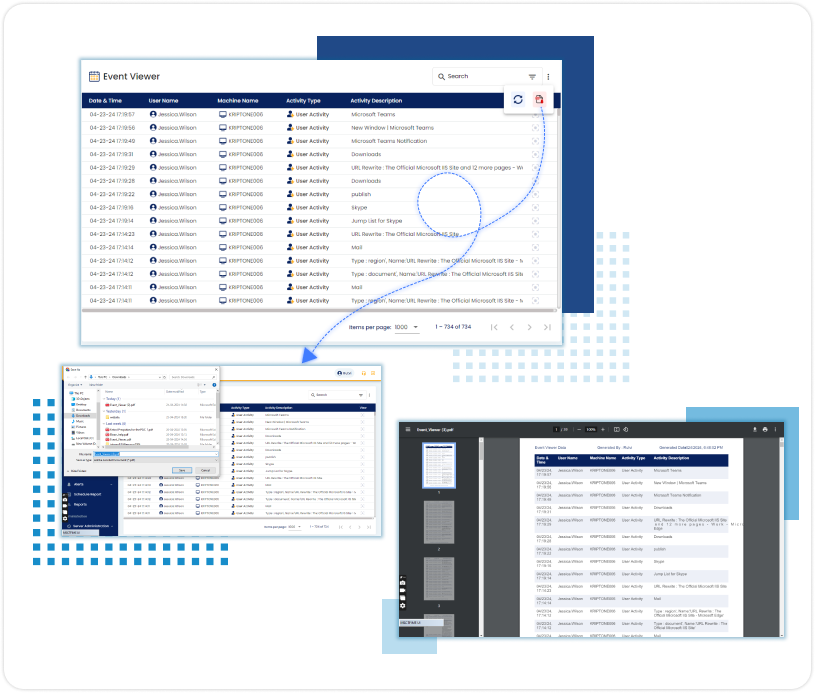
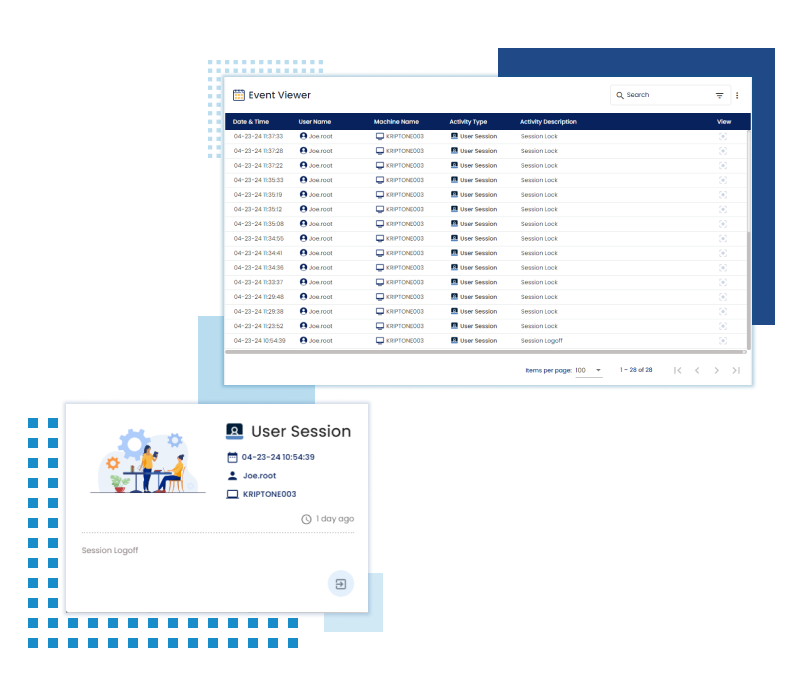
Session Activities (Log In/Log Out)
Capture Screenshots Taken
Capture and analyze screenshots to identify instances of sensitive data being displayed or shared without proper authorization.
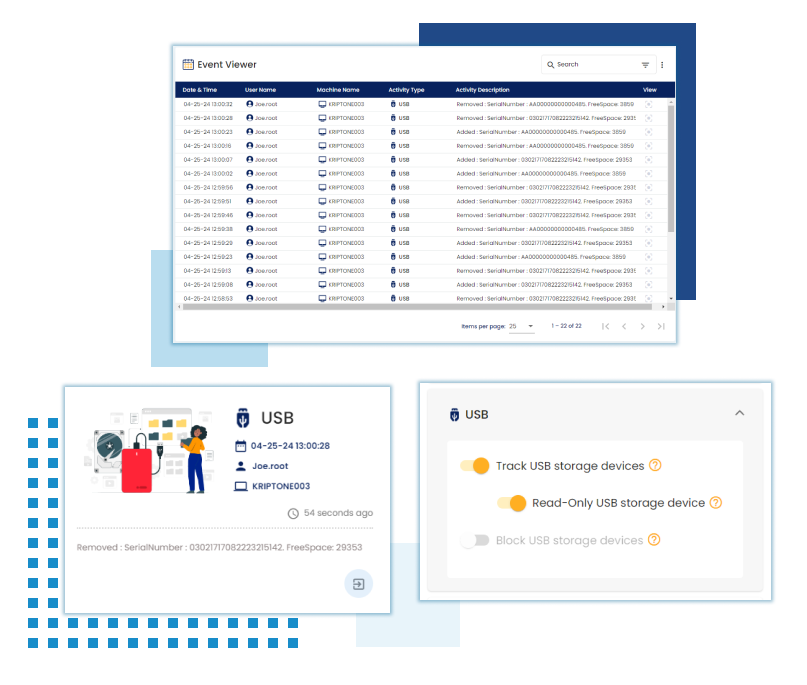
USB Monitoring
Monitor USB device connections and data transfers to prevent unauthorized copying or transfer of sensitive files.
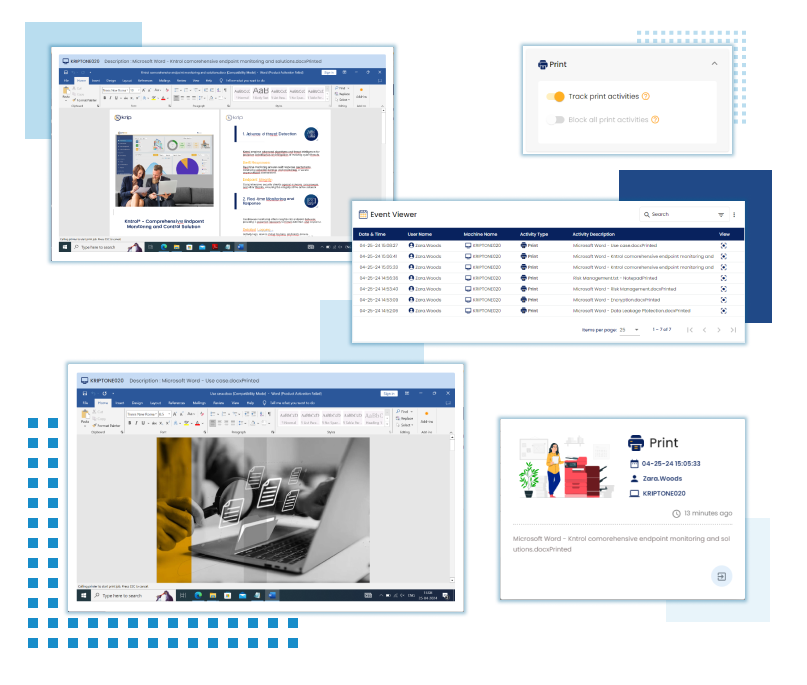
Print Tracking
Track print activities to monitor and control the printing of confidential documents and prevent data leakage through hard copies.
Tracking Clipboard Data Transfer

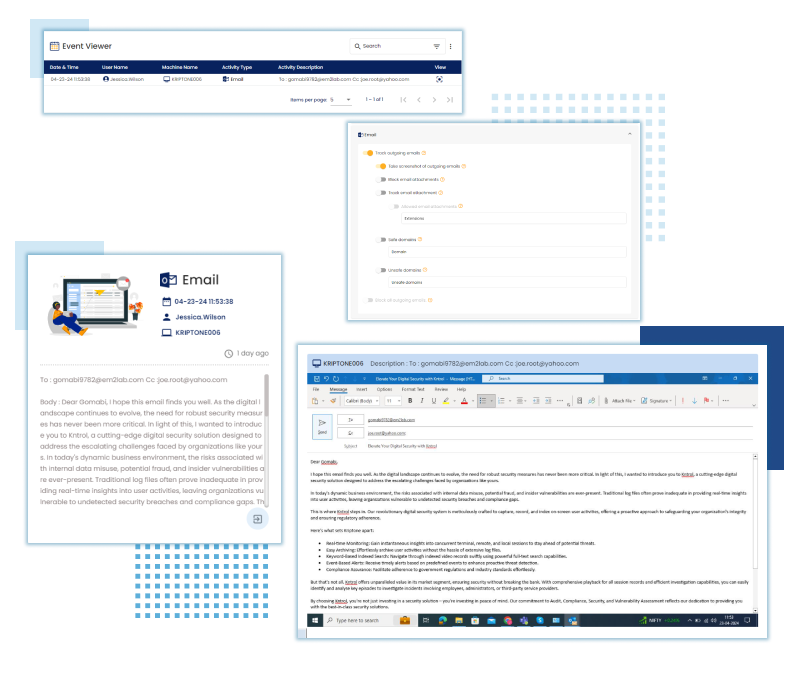
Email Activities
Monitor email communications and attachments to prevent the unauthorized sharing of sensitive data via email.
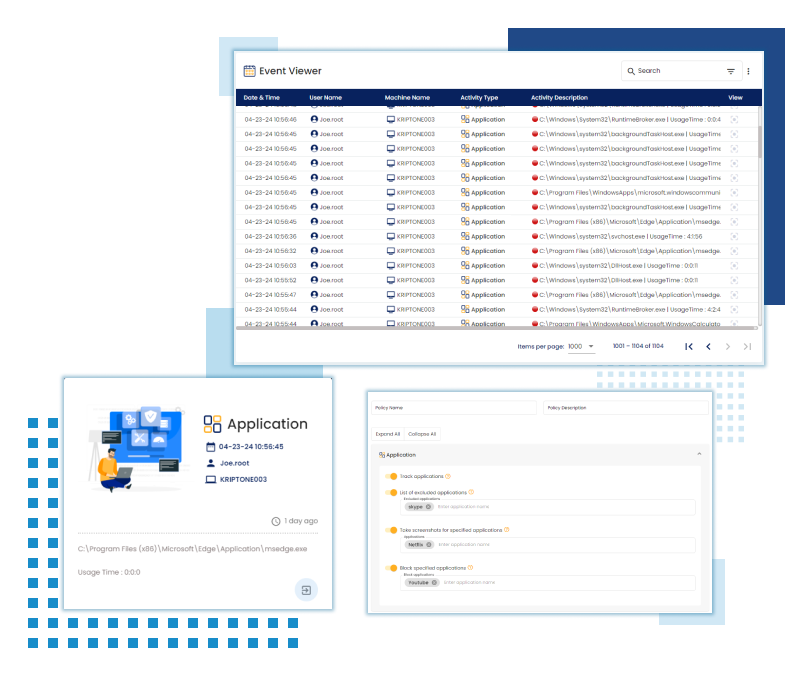
Application Monitoring
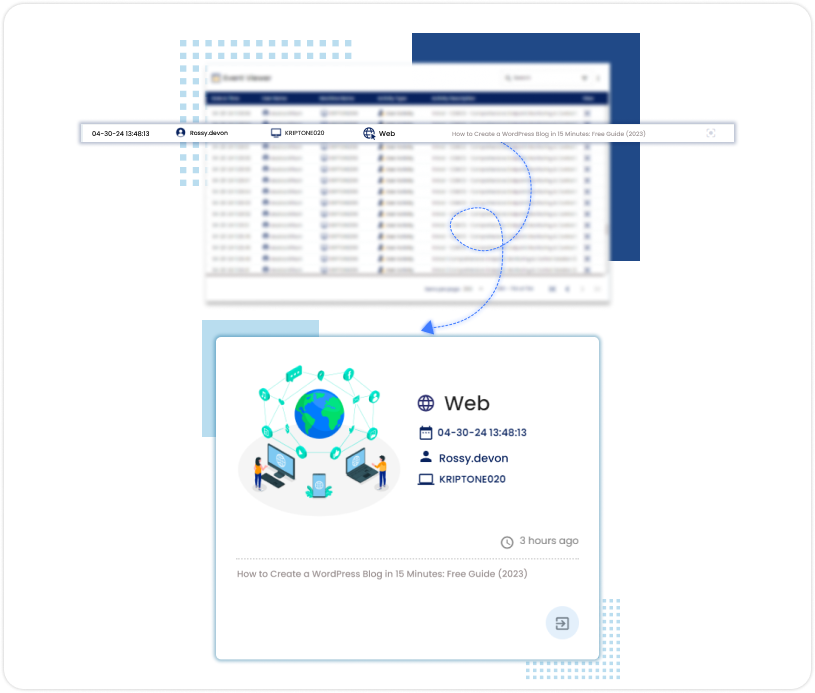
Web Tracking
Track web browsing activities to identify and block access to websites or services that pose a risk of data leakage or unauthorized data access.
Controlling And Blocking Features
Application Control
Control access to applications based on predefined policies to prevent unauthorized use of applications that could lead to data loss.
USB Control
Block or restrict the use of USB devices to prevent data transfer to external storage devices without proper authorization.
File Tracking
Track file movements and modifications to ensure data integrity and prevent unauthorized access or modifications.
Two-Factor Authentication
Implement two-factor authentication to enhance security measures and prevent unauthorized access to sensitive data.

Screenshots Restriction
Restrict the ability to take screenshots of sensitive information to prevent unauthorized capture and distribution.
Print Blocking
Block printing of sensitive documents based on predefined policies to prevent data leakage through hard copy output.
Automatic Watermarking on Screen Capture
Automatically watermark sensitive documents or files displayed on the screen to deter unauthorized sharing or distribution.
Reporting Features
Alerts
Alerts Features
Generate real-time alerts for suspicious activities or policy violations related to data loss, enabling immediate response and mitigation.
Risk Ranking
Risk Ranking Features
Generate comprehensive reports summarizing data loss incidents, policy violations, and compliance status for auditing and regulatory purposes.
Policy Scheduler
Policy Scheduler Features
Schedule regular audits and policy enforcement checks to ensure continuous compliance with data protection policies and regulations.



