Defend Sensitive Data From
Kntrol, Build To Protect
Kntrol - Proactive Security and Compliance.
Kntrol is a Smart security tool that monitors people’s behaviour to prevent harmful incidents. It provides visibility for everyone to stay informed about any unusual activities, ensuring prompt action if something seems wrong. Additionally, Kntrol enforces compliance with regulations to maintain a secure environment.
Behavior Pattern Tracking
Kntrol goes beyond simple monitoring by actively tracking and analysing behaviour patterns. By doing so, it identifies anomalies and potential threats before they escalate.
Enhanced Organizational Visibility
Kntrol provides comprehensive visibility across the organization's endpoints. This allows administrators to have a clear understanding of the security posture and potential risks, enabling proactive threat mitigation.

Policy Compliance
Kntrol ensures compliance with defined security policies and regulatory requirements. Through its robust features, it enforces adherence to established protocols, reducing the risk of breaches and ensuring regulatory compliance.


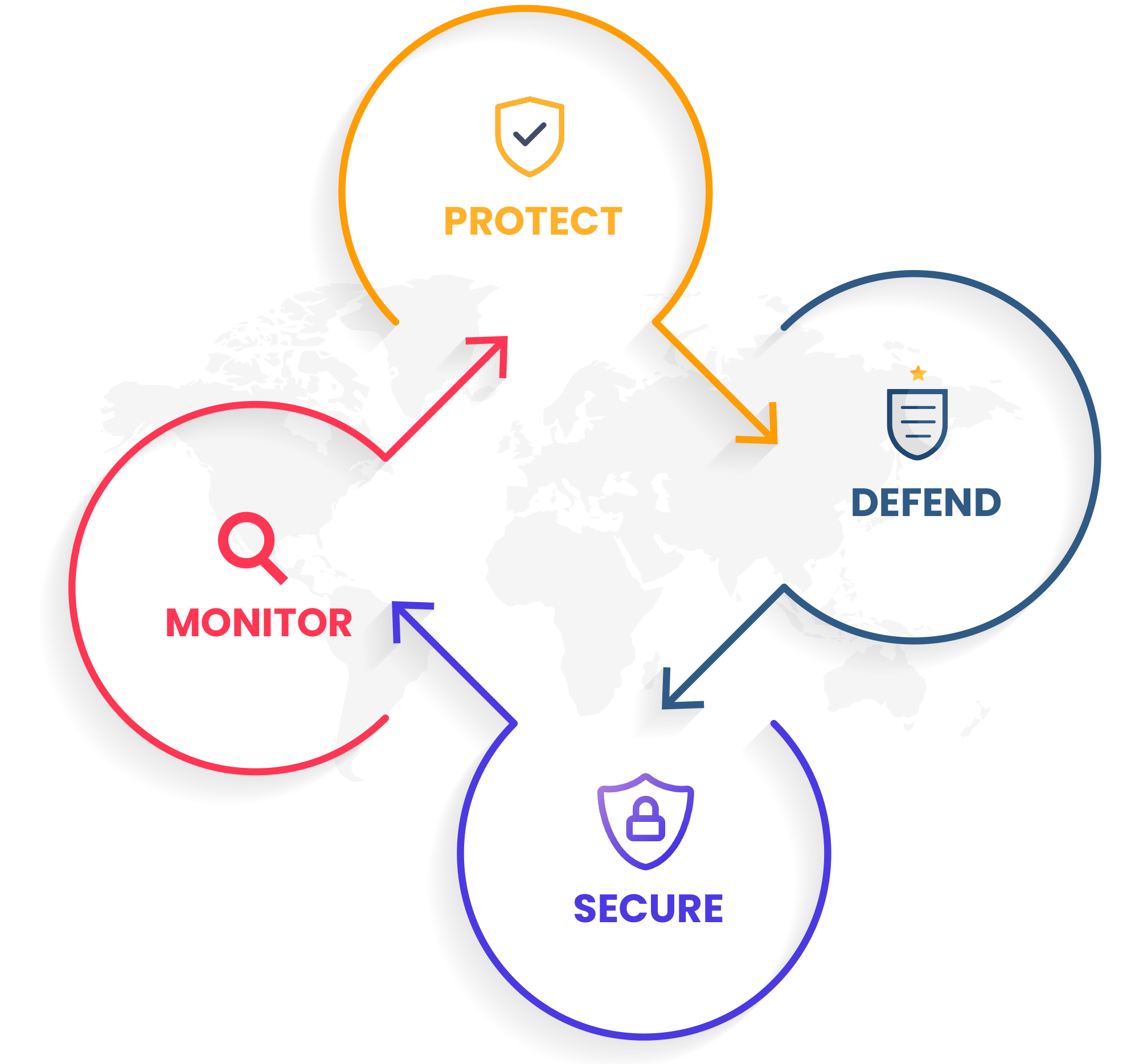
Protect.Defend.Secure
Protect
Protect
Defend
Defend
Secure
Secure
Try with the best
Our Services
User Productivity Monitoring
Security Incident Investigation


Insider Threat Prevention
Endpoint monitoring helps in identifying potential security threats, such as malware infections, unauthorized access attempts, or suspicious activities on endpoints. It enables organizations to proactively respond to and mitigate these threats before they can cause significant damage.

Insider Threat Prevention
Endpoint monitoring helps in identifying potential security threats, such as malware infections, unauthorized access attempts, or suspicious activities on endpoints. It enables organizations to proactively respond to and mitigate these threats before they can cause significant damage.
Governance and Compliance
Many industries have specific regulations and compliance requirements related to data protection and privacy. Endpoint monitoring helps organizations ensure that endpoints are in compliance with these regulations. It can monitor software installations, security patch levels, user access controls, or data transfer activities to maintain regulatory compliance.

Governance and Compliance
Many industries have specific regulations and compliance requirements related to data protection and privacy. Endpoint monitoring helps organizations ensure that endpoints are in compliance with these regulations. It can monitor software installations, security patch levels, user access controls, or data transfer activities to maintain regulatory compliance.
Start your Kntrol Experience
Manage insider risk, optimize productivity, and enforce compliance with kntrol.
Start your Kntrol Experience
Manage insider risk, optimize productivity, and enforce compliance with kntrol.






